There is a great article by Yan Cui that covers how to leverage Route53 subdomain delegation to simplify the creation and validation of Certificate Manager SSL certificates in an AWS multi-account environment.
In addition to having a multi-account setup, we needed to create public DNS records for the production environment at the top level of the domain, for example, lower environments in the “dev” and “test” accounts were OK as: “myapp.dev.mydomain.com” or “myapp.test.mydomain.com”, but we needed production to obviate the “prod” part and look like “myapp.mydomain.com”.
To achieve the desired outcome, we came up with a variation of the subdomain delegation strategy, such that:
- We have a management (or master) account where the purchased domains reside, no Route53 hosted zones there
- The main nameservers for the domain point to a “root” hosted zone created in the production AWS account
- Subdomain delegation is used to give the lower environments AWS accounts their own “local” hosted zone
Because a picture is worth a thousand words, and for engineers, a diagram even more :), here is how such setup looks like:
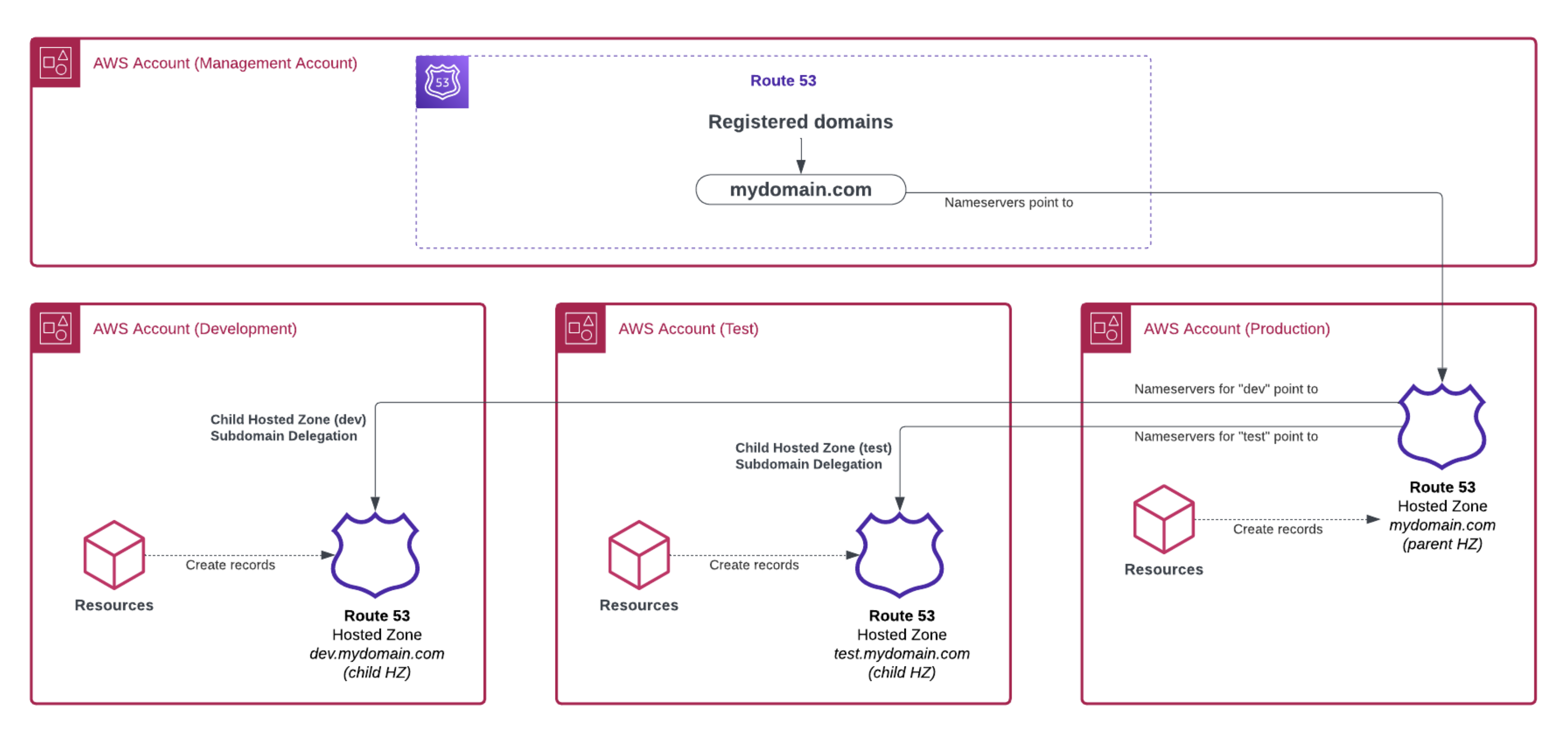
In our case, we used Terraform with multiple providers (pointing to the multiple AWS accounts) to stitch the Route53 pattern together and it was relatively easy to implement.
There you have it, if you have the additional requirement to have production hostnames without an environment level in them, the pattern described here can works good!
For a detailed explanation of the subdomain delegation logic, and how to implement it, the original article of Yan Cui is a great reference:
https://theburningmonk.com/2021/05/how-to-manage-route53-hosted-zones-in-a-multi-account-environment/