When leveraging AWS Control Tower to extend the capabilities of AWS Organizations to manage multiple AWS accounts, one of the perks is that the newly created landing zone is set up with a pre-configured directory that helps you manage user identities and single sign-on, so that your users have federated access across accounts. When you set up your landing zone, this default directory is created to contain user groups and permission sets.
You can use this functionality to easily provision new roles to the target accounts, and associate it to Users within your organization through a centralized Single Sign-on access screen.
How it Works
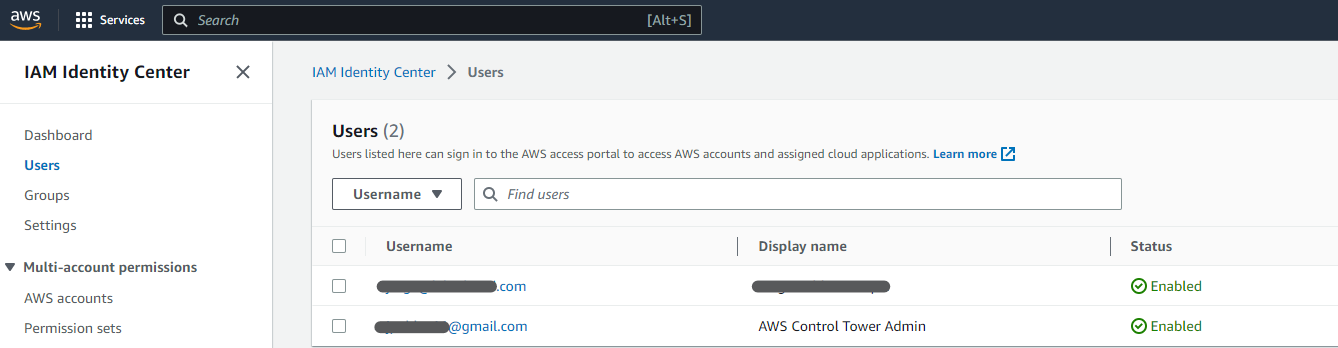
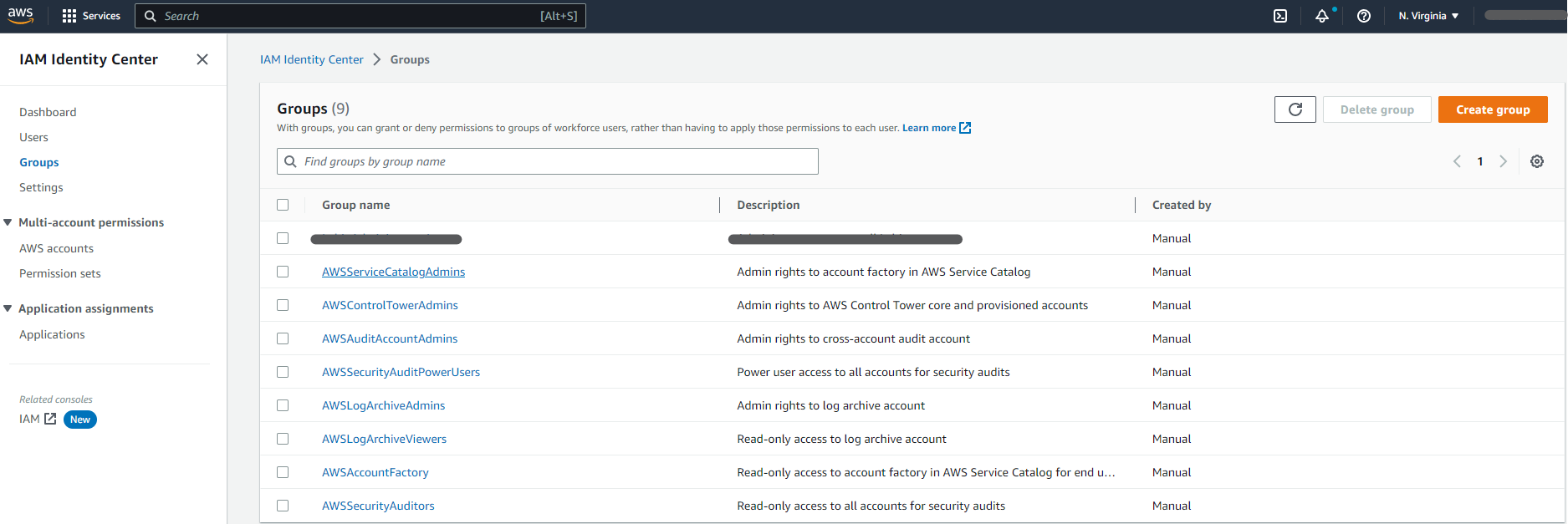
Users and Groups
These two sections are pretty straightforward, you can create users and associate them to Groups, the recommendation is that you manage your permissions on a group level to simplify management, even when IAM Identity Center might allow you to associate Permission Sets to Users directly (that’s a no, no .. ;))
What is a Permission Set?
You can think of a Permission Set as a template that describes a role and its associated permissions, but it is just a logical definition that fully resides in IAM Identity Center until you provision it to AWS Accounts.
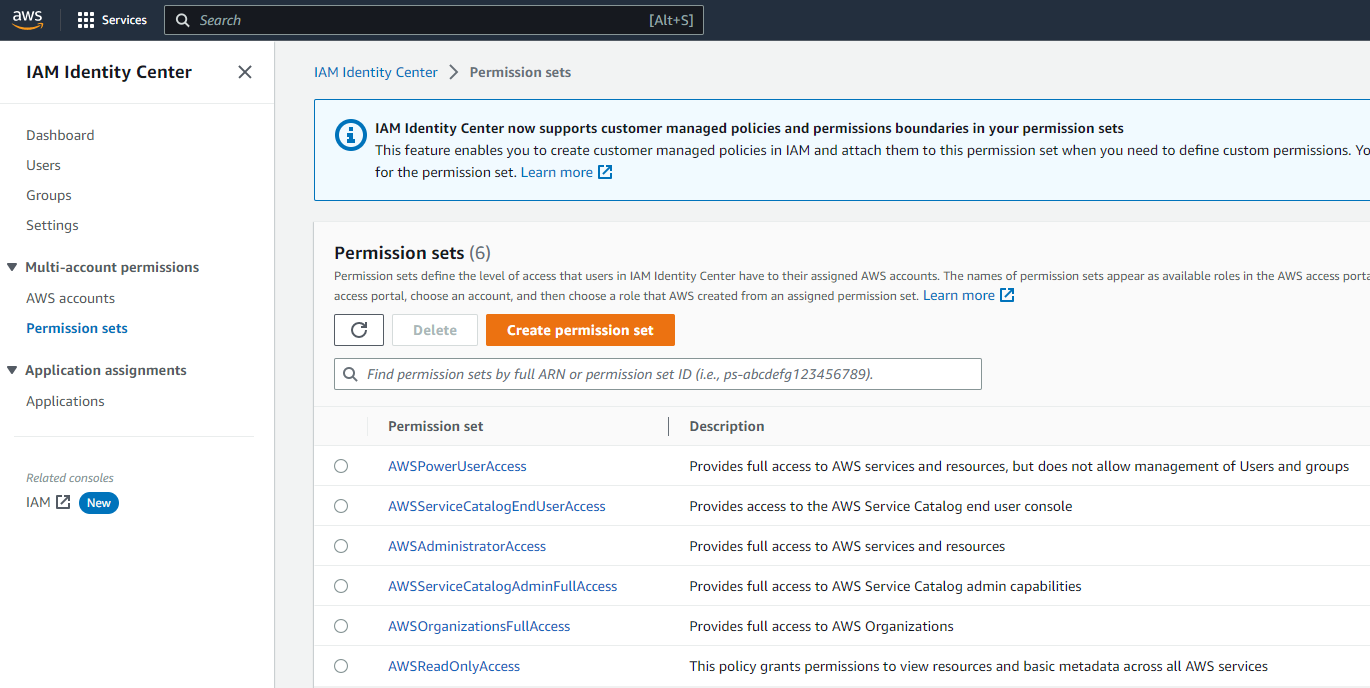
You can associate AWS-managed or Customer-managed policies to a Permission Set, and once provisioned in a target account, they become traditional IAM roles that look like this:
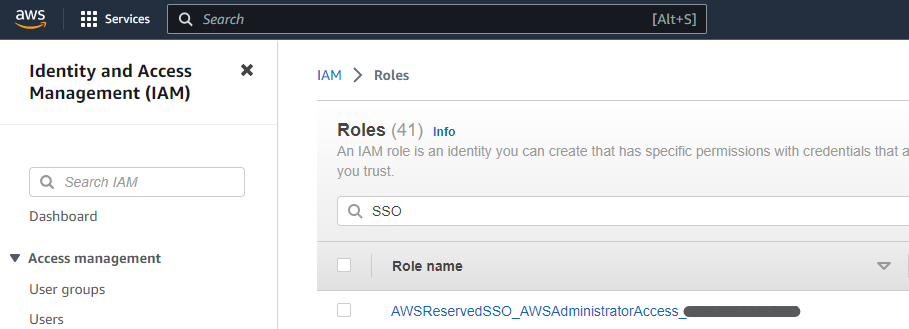
How a Permission Set Becomes an IAM Role in the Target Account?
Short answer: you associate a Permission Set to a User or Group in a target AWS account, did I say that right? :/
This part can be a bit confusing, but it is maybe more clear with an example and some screenshots.
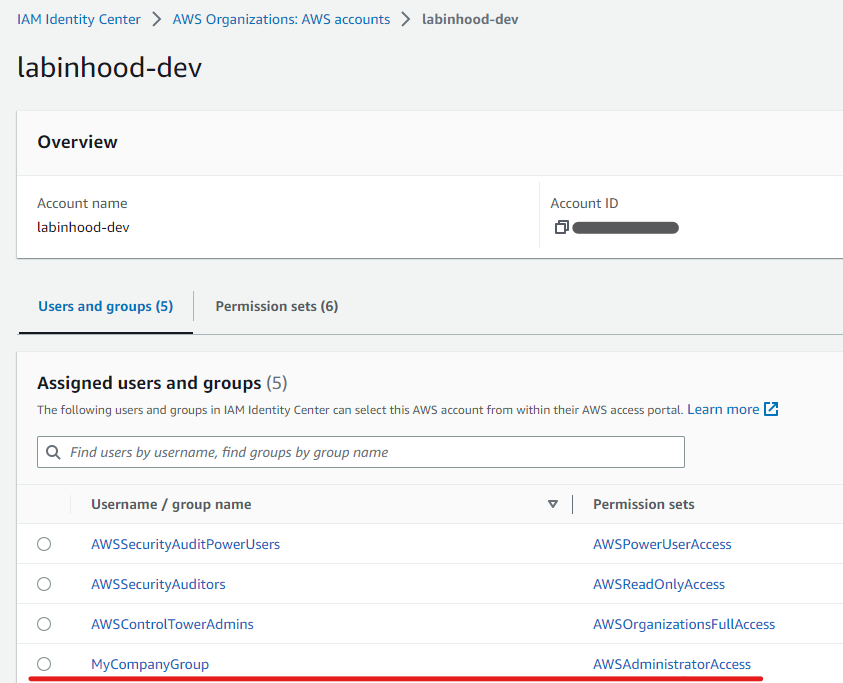
Let’s say we want to grant “AdministratorAccess” to users that belong to the “MyCompanyGroup” group, for the sake of simplicity let’s assume the Group has already been created and Users added to it.
First, you click on “AWS accounts” on the left navigation menu in IAM Identity Center:
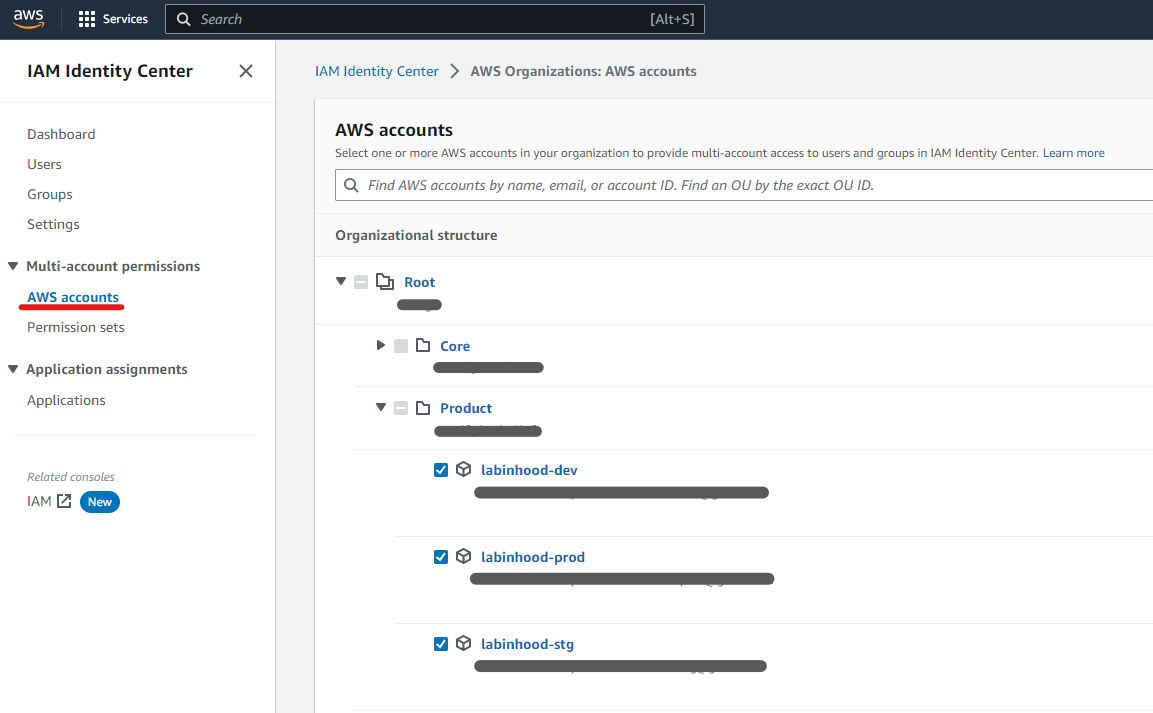
Then you click on the “Assign users and groups” button (top-right corner), select the Group or Groups that will receive the new Permission Set (or role in the target account once provisioned).
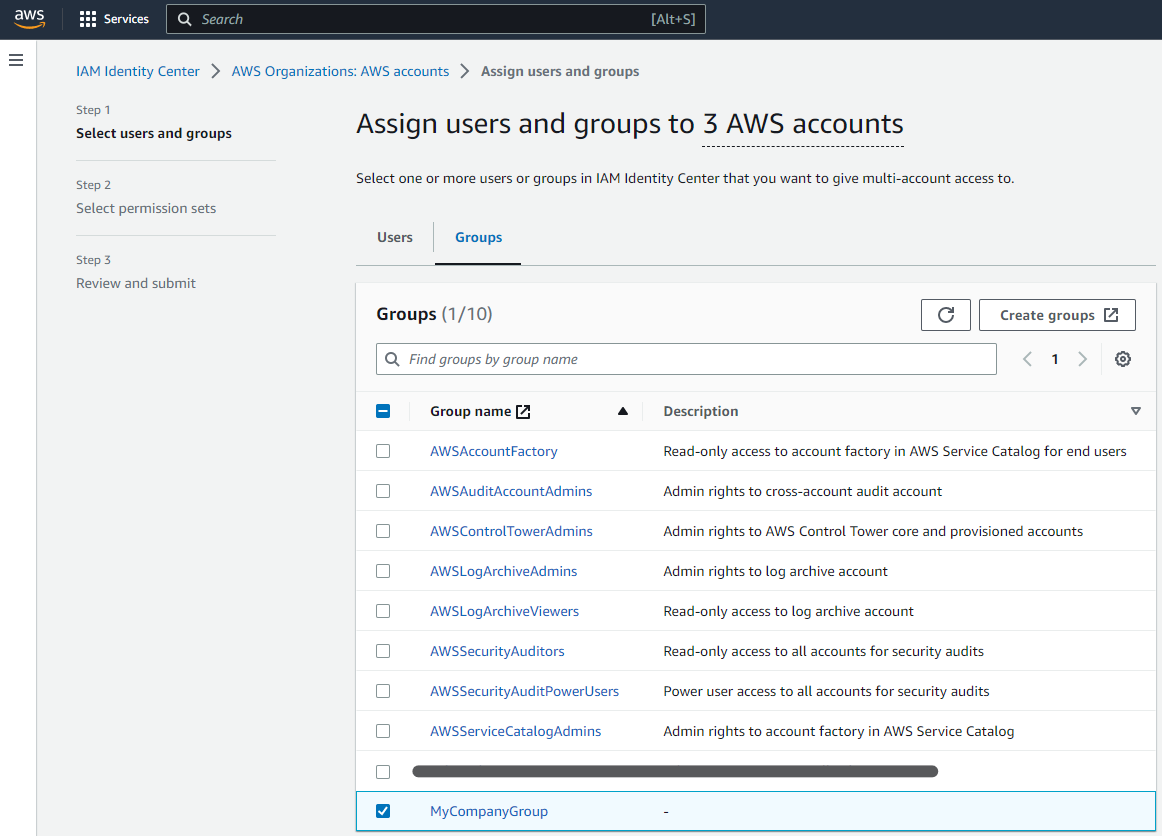
On the next screen, Permission Sets finally join the game!, pick one or multiple Permission Sets the User or Group will receive in the target account (remember, stay away from direct User associations if you can, and manage all permissions through Groups for cleaner and easier management).
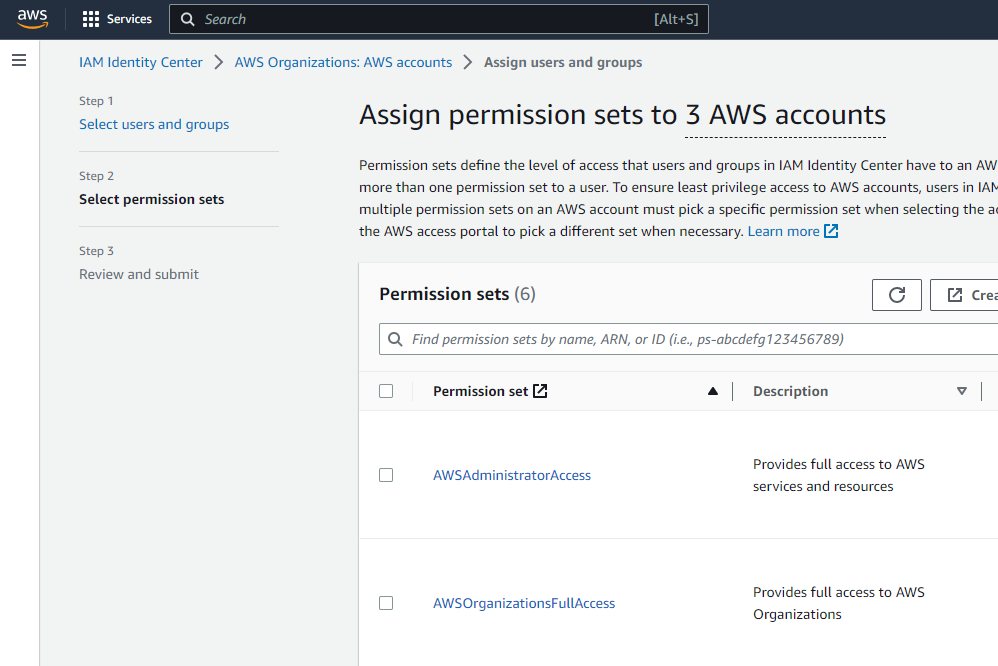
A summary is presented in the next screen and clicking the “Submit” button starts the magic.
If an IAM role does not yet exist in the target account for the Permission Set, it will be provisioned on the spot, otherwise the existing one is used, this ensures only one. “instance” of a Permission Set exists in the target account.
Also, if you update a Permission Set after it has been provisioned in target accounts (e.g. you add a new policy to it, etc.), IAM Identity Center reprovisions it in all associated accounts and applies the updates, how cool is that?
This is how the Group to Permission Set association looks like once provisioned in IAM Identity Center (“AWS accounts” section > [Specific AWS account screen]):
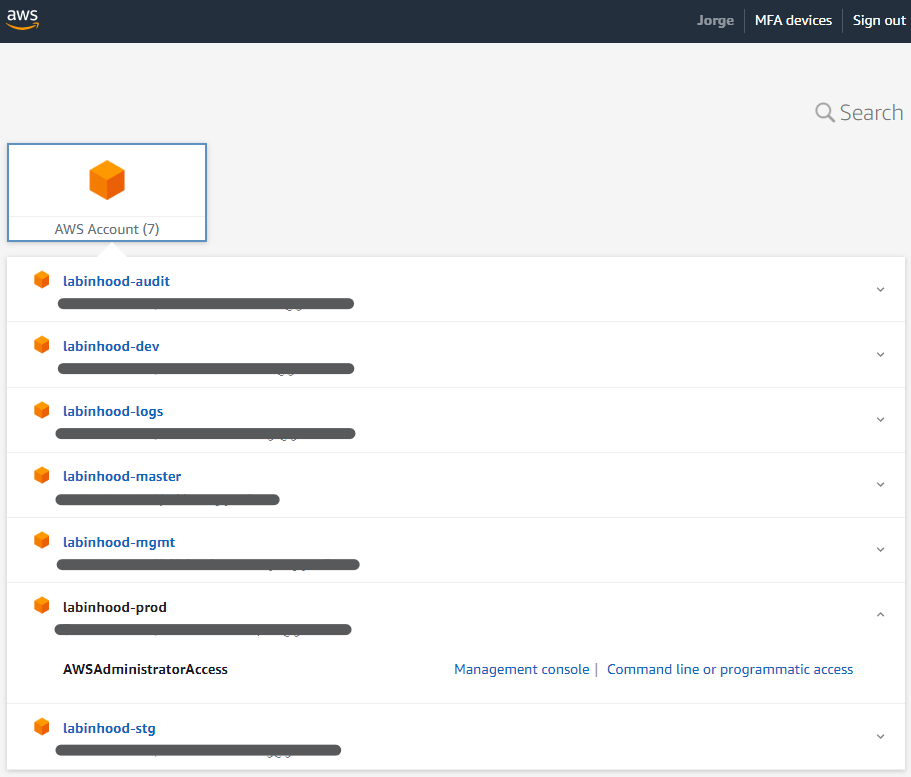
What the User Sees
Once an organization user logs into the Single Sign-on portal provided by AWS, they get a list of accounts and roles within they have access to, all of this managed by the mechanisms and principles that we just explored above:
Conclusion
Control Tower and IAM Identity Center greatly simplify the management of permissions across multiple AWS accounts within the same AWS Organization, give it a try!
References
https://docs.aws.amazon.com/controltower/latest/userguide/sso.html